You have a vast number of priorities on your plate as a small business owner / manager, the pressure from which has only grown with the chaos and change brought to all of our businesses during 2020; despite this, the security of your data should remain very near the top.
Cybercrime is one of the biggest threats to the sanctity of our livelihoods in this digital age, and, this year alone, a Hiscox report shows a UK small business is successfully hacked every 19 seconds¹ from a base of 65,000 attempted attacks on small to medium sized businesses each day.
The momentum, timelines and sophistication of attacks is continuing to build too, with the UK’s NCSC (National Cyber Security Centre) reporting one in four attacks is related to COVID-19² – leaning on the pandemic as a distraction to capture businesses at a vulnerable point.
Whichever industry your business trades within, your IT system holds the key to your operations and your finances, and that very system is under attack. Whether that is your customer information, intellectual property or the cash within your bank accounts – cybercriminals are going to great lengths to hack or dupe their way into your network.
Small businesses are not immune to the threat.
Unlike many larger corporations, small businesses rarely possess the technical infrastructure or budget to implement comprehensive defences, and this shows – a UK Government report flags concerning statistics that highlight that despite the majority of reported attacks taking place among large and medium enterprises; the majority of small businesses do not have sufficient means to report and act on cyberattacks, nor potentially even identify when they have become a victim³.
That said, a small business need not directly invest tens of thousands in the same grade of cyber security defences as a bank. There are a number of other cost effective and more accessible forms of protection that could be implemented to achieve the desired effect.
Gone are the days of needing specialist technical skills to execute a profitable cyberattack for the hacker, a new breed of low-skill con artists that can quite literally piggy-back on the foundations laid by those they seek to imitate. With email phishing and ransomware attacks the most common of cyberbreach that results in financial loss within a small business, it could never be more important to defend the areas of your IT infrastructure most vulnerable to these types of attack.
Why do I need to secure Microsoft 365?
To effectively defend your business from cyberthreats, there are a wide array of different technical tools, policies and procedures, and IT user education that you need to implement. Most small businesses will be somewhere along this journey, perhaps having anti-virus software installed, a firewall configured and a secure password policy in place – but does that go far enough?
The vulnerabilities of email.
Despite having cyber defences and protocols in place, as the lifeline for modern communications, email traffic must still readily flow in and out of our businesses.
It is getting more and more difficult to determine a malicious email from a genuine one – two of the most common forms of email phishing attacks, include –
The cybercriminal masks themselves as a company employee / director.
As one small example of a repetitive issue globally, a known pharmaceutical distributor fell victim to a cybercriminal masking themselves as the company’s Chief Financial Officer.
An email was sent to the finance team, masked as being sent from the CFO’s personal mailbox, instructing immediate payment be made of £25,000 to a particular bank account. Further adding to its validity, the email even contained the CFO’s correct and full email signature.
Unfortunately for the business, the finance team did as the email instructed and paid a cybercriminal £25,000 without question.
The cybercriminal masks themselves as a known brand or company.
An example which may sound familiar on a personal level, known companies, brands and even Government departments are often imitated.
Throughout the COVID-19 pandemic especially, countless fraudulent emails were sent purporting to be from the HM Revenue and Customs (HMRC) – using the lure of tax rebates and COVID related support funds to draw in the unsuspecting.
A slightly more sophisticated approach, a recent example has been seen to successfully mask itself as an email from Netflix. The message, designed to capture card details, claims that the recipient’s bank information is due for renewal. By only glancing at the email once, trusting the brand name – and as an existing customer – hundreds have fallen victim.
How ransomware can slip through.
Lurking on the internet in many different forms, malicious software (known as Malware) – particularly ransomware – lays in wait to infest itself in your network. Designed to remove your access to data by encrypting your files behind a secure key, which is held only by the cyber attacker, a ransomware breach quite literally holds your data to ransom.
Malicious links or scripts embedded within files that otherwise appear innocent are the most common ways Malware will download and install itself on to your network. Two of the most recent and common examples, include –
A document shared via OneDrive that contains a malicious link.
Users have been duped into opening a genuine email with a file share link from a Microsoft OneDrive user – a link easily clicked as often the email is sent from a known contact or associate with whom you have previously exchanged emails.
Contained within the OneDrive file is a file that presents itself as a PDF file (and therefore likely safe to open), which is in fact an image – as you click on the image to open the PDF file, the user is taken to a malicious weblink that unknowingly opens a download installer in the background.
An Excel spreadsheet ‘invoice’ that contains a Macro script.
Another common threat, most often seen in the form of Excel spreadsheets emailed to recipients purporting to be an invoice – unleashes its malicious software once the script inside the document is activated.
Should a user receive a document from a trusted email source, unwittingly open it, and run the embedded macros – the Malware takes hold in the background unbeknownst to the user.
What would happen if my Microsoft 365 account is breached?
Dependent on the goals of your cyber attacker, any number of outcomes could take place. At the highest level, these could include any one or more of the following –
- Data theft or corruption
The file data you have contained within your OneDrive and SharePoint libraries could be corrupted, stolen, deleted – or a combination of the three.
- Sensitive data theft
If the data that you hold contains password credentials for third-party systems, or worse, bank or card details for your own business or of customers’ – this could be specifically targeted or stolen among your other file data.
- Email and chat contents
Any of your email or Teams / Skype chat correspondence could be trawled and sensitive information contained within that history be used for further malicious purposes.
- Mask as your business
With access to your Microsoft 365 environment comes the visibility of your contacts and correspondence history. The cybercriminal learns with which businesses and individuals you regularly transact, arming them with a list of unsuspecting potential victims to target – likely masking themselves as your own business to do so.
Microsoft 365 at the heart of business.
From storing email, files & folders to other sensitive financial or customer records – to name but a few – Microsoft 365 is the cloud ecosystem at the very heart of small business day-to-day IT use; and, with this gate left slightly ajar to readily consume email, it is inevitable that malicious email messages will get through – so we must do what we can to protect that environment.
Despite being a SaaS (Software-as-a-Service) solution, with its own security and compliance featuring as a part of the infrastructure defences provided by Microsoft as part and parcel of the service, the front-end end user aspects (within your own control and outside of Microsoft’s), must be protected.
How to approach securing Microsoft 365?
There are two key areas to address to reduce risk of data breach and best secure Microsoft 365 for your small business:
- Policy changes for how your users access and use 365
- Implementation of technical controls, policies, filters and defences.
Your users.
The users of a system can be both the final line of defence in preventing a system breach, or the inadvertent cause of a breach. A see-saw balance between success or failure that can be tipped in the wrong direction with something as simple as clicking on a malicious link in the wrong email.
There are a number of risks posed by the way users access and interact with Microsoft 365, that depend upon:
- The complexity of their password and whether this password is unique to 365 or used as a general password across other services
- The level of system access and permissions assigned
- The ability to share files and documents, and to whom
- The ability to share potentially sensitive information within email messages
Your technical defences.
To take a step further beyond the user-focused protocols, technical defences exist within Microsoft 365 to overcome a variety of different security threats, including:
- Malware, ransomware and other malicious file attachments being received or downloaded from malicious emails
- Email content or attachments from being intercepted or viewed by unauthorised parties
- Phishing attacks being received or having their links clicked upon within email
- Your domain becoming a victim of a ‘spoofing’ attack with cybercriminals purporting to be your business
Security options within Microsoft 365
Which security features are available ‘out of the box’, which risks they tackle and how to apply them.
Login security.
The risks.
Reduce the risk of individual user accounts from becoming breached by cybercriminals as a result of exposed credentials on the dark web, or, because of accounts being secured with basic common password formats.
Overcoming the risks.
A secure password policy is defined by default within Microsoft 365 and is designed to enforce users to adopt the structure of a best practice ‘complex’ password. A complex password is one that cannot be easily guessed, is of a certain length, and is a mixture of numbers, letters and special characters.
The attitude to secure password best practice has changed in recent years, with a traditional approach being to enforce users change passwords on a cycle of every number of days or weeks – and in some cases – enforcing passwords of ever greater length and complexity.
In more recent times, this has been rethought. Enforcing longer passwords, combined with a regular password renewal cycle, simply forces users to simply repeat their same password format – recycling the same core lettering, but simply extending it by adding a number of further characters at the end. Resulting in the objective of making their account more secure entirely defeated.
Instead, applying an additional layer of login security, known in some cases as 2-Factor Authentication (2FA), or more commonly now, Multi-Factor Authentication (MFA) is the better approach.
MFA is a second authentication step that takes place after a user has entered their password. Accounts are further secured by requesting the user input a code, which changes on a cycle of every few seconds (or upon each login attempt) – the code is provided to the user via their mobile device through text message or by accessing an authentication app.
MFA, among other login security best practices, can be enforced for your tenancy through Microsoft 365 security defaults.
What are Microsoft 365 security defaults?
To define security parameters that apply globally across all of your users, (and for any subsequently added user accounts), you can activate security defaults that enforce a number of policies automatically.
Security defaults are available to all users of Microsoft 365 at no extra cost, provided you are an organisation that utilizes at least the free tier of the Azure Active Directory service.
Security defaults include:
- Require all users to register for MFA
- Require all system administrators to perform MFA
- Block legacy forms of authentication
- Require users to perform MFA actions upon certain actions
How to implement Microsoft 365 security defaults?
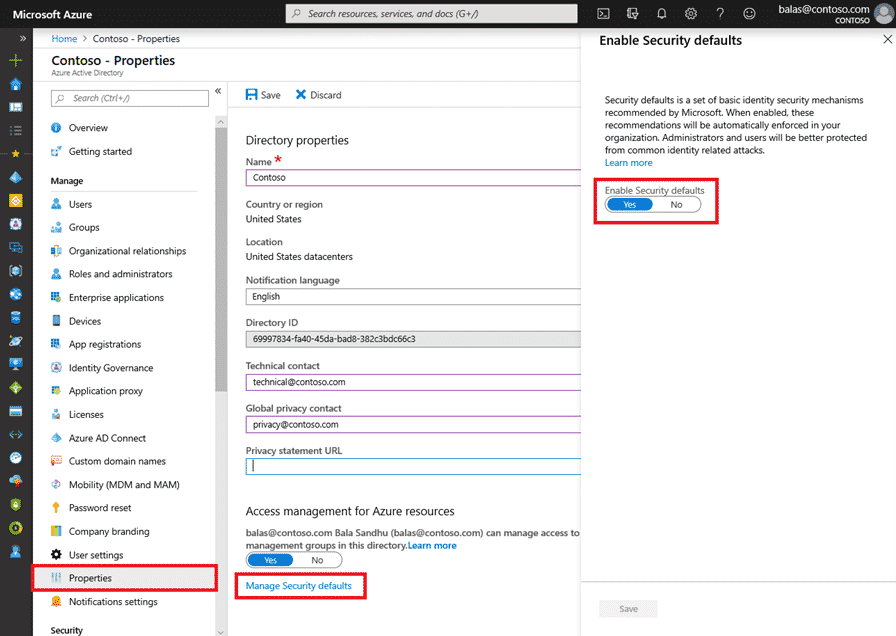
To implement the security defaults globally within your Microsoft 365 tenancy, follow these steps:
- Visit your Azure Portal (https://portal.azure.com)
- From the main menu scroll to ‘properties’
- Click ‘Manage security defaults’
- Move the slider across by clicking ‘Yes’
Access security.
The risks.
If access to files, folders, document libraries and email is not secured on a ‘need to know’ basis, your team will have carte blanche visibility of documents and data outside of their job role and responsibilities, (some of which may be sensitive and subject to protection under legislation).
More concerningly, should an individual account suffer a breach, a cybercriminal will be provided with unfettered access to your entire environment – permitting scope for unfathomable levels of theft and corruption.
Overcoming the risks.
Controlling access within Microsoft 365 can be easily achieved by structuring your files & folders and the delegation rights to view and edit that data.
Files are typically best organised departmentally – such as, finance, sales and marketing. The user permissions are granted among the team members within each of the respective departments. Depending on the individual’s grade, permissions can be further broken down to restrict junior team members from accessing files destined for management.
Alternatively, files could be organised within document libraries styled by client or by project. The same user delegation process applies.
Users are not pigeon holed into one department either – if you are a member of management, or have people within functions that cross-department, multiple permissions may be assigned.
Such permission sets are defined within Microsoft 365 as groups.
What are Microsoft 365 groups?
To provide access to resources and a commonly assigned set of permissions against a group of users, a group must be setup within Microsoft 365.
These groups can be defined from a high-level, through the administration portal, or created in the background by the system automatically upon creating a new SharePoint Library or a Teams Channel – and defining the user permissions in those front-end applications.
Different types of permission groups exist within 365:
- Microsoft 365 groups – (formerly Office 365 groups) are used for collaboration between users, whether inside or outside of your organisation
- Distribution groups – are commonly used as a group email list – such as [email protected] being an email address used to email multiple users
- Security groups – are used for granting permissions to specific resources, such as SharePoint sites and Teams channels
- Shared mailboxes – provide multiple users with parallel access to a single email mailbox
How to create and manage Microsoft 365 groups?
Your active groups (across all of the previously outlined types) are accessible by visiting https://admin.microsoft.com/adminportal/home?#/groups and logging in with your administrator credentials.
From here, you can add a new group and define the users you wish to include within that group; while also being able to see and manage groups created elsewhere within your Microsoft 365 environment, such as directly within SharePoint or Teams.
Permissions for external sharing in Microsoft 365.
There are a number of granular controls in place to define whether and how data can be shared externally. Two distinct differences exist within 365 between different types of external users; external access provides access to all of the users within an entire domain and guest access permits permissions to an individual.
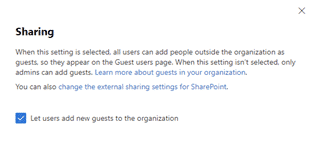
To control whether to permit external users to be added as guests:
- Visit the admin portal, https://admin.microsoft.com/AdminPortal/Home#/Settings/SecurityPrivacy
- Click ‘Sharing’
- Tick or untick the box
To control whether to permit external sharing from SharePoint:
You may define this globally at your organisation level or set this permission individually within a specific SharePoint site.
If a SharePoint site’s external sharing option and the organisation level permission do not match, the most restrictive rule will apply.
To control whether to permit external sharing from Teams:
Guest access must be authorised separately for Microsoft Teams.
Prevent emails from being automatically forwarded externally from Microsoft 365.
To retain control of your email content and to prevent any email from inadvertently leaking outside of your internal environment, you may wish to disable users the ability from being able to set an email rule that automatically forwards email to external email addresses.
To enable or disable this rule for your tenancy, follow the steps and video shown here⁸.
Cybersecurity defences.
Beyond the tools and features designed to secure access to your Microsoft 365 environment, and those policies we have listed that mitigate the risk of loss, a number of other cybersecurity defences exist to go even further in the effort to protect your data.
Malware protection.
The Microsoft 365 ecosystem contains protection as standard against malware, however this functionality can be further increased in capability by blocking certain file types that are most commonly associated with malware.
This can be implemented by:
- Visit https://protection.office.com/ and login with your admin credentials
- In the Security & Compliance Centre, on the left-hand navigation, beneath ‘Threat Management’ select ‘Policy’ > ‘Anti-Malware’
- Double-click the default policy to edit this organisation wide policy
- Select ‘Settings’
- Under ‘Common Attachment Types Filter’ select ‘On’.
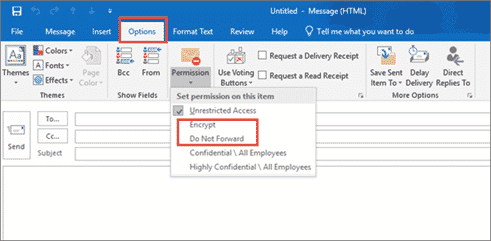
Email encryption.
Microsoft 365’s email encryption function helps ensure that only your intended recipient can view your email content. Aside from encryption, you can also define permissions by which your recipients are restricted on the actions they can take with your email – such as blocking the email from being forwarded, printed or the content copied elsewhere.
To send protected email:
- In Outlook for Windows, select the ‘Options’ tab and click ‘Permission’
Anti-email phishing.
Anti-phishing technology, ‘Safe Links’ as a part of the Microsoft Defender service, can help protect your users from inadvertently clicking malicious website links within emails or other files. Safe Links provides time-of-click verification of web addresses within emails and Office documents and how this service acts can be defined within the Safe Links.
This can be implemented by:
- Visit https://protection.office.com/ and login with your admin credentials
- In the Security & Compliance Centre, on the left-hand navigation, beneath ‘Threat Management’ select ‘Policy’ > ‘Safe Links’
There are options to alter the system defaults depending on your requirements. More information can be found here⁹.
Email spoofing.
Your custom domain can be protected from being ‘spoofed’ through Microsoft 365’s anti-phishing protection. This protection includes the support of email security best practices including, SFP, DKIM and DMARC protocols.
The implementation of such controls can be quite complex with a number of steps involved. It is advised you seek the expertise of a Microsoft 365 consultant, such as Edge IT, to correctly configure these protocols.
Best security practices to apply
This article has presented a number of ‘belt and braces’ security options to consider implementing within your organisation, some of which however may not be entirely necessary within your organisation – depending on the way you work.
There are however, a number of these components, that cloud security experts such as ourselves at Edge IT, will always recommend are implemented as standard. These include:
- Enforce security defaults – especially MFA among all of your users
- Structure your files and folders in an ordered way within SharePoint sites/libraries or Teams channels – associate users and permissions appropriately
- Educate your users about email phishing and ransomware, particularly how to look out for suspicious files and links
‘Cloud-Native Authentication’ – modern authentication in the cloud.
There are other considerations which are brought to mind from the advice contained within this article, namely the way in which users authenticate with their cloud services. Microsoft 365 relies upon the user administration contained within its sister cloud platform, Microsoft Azure. For free, all 365 environments are provided with access to Azure Active Directory, from which the usernames, passwords and login security may be controlled.
If you are a business with more of a traditional ‘on-premise’ IT setup, your active directory will likely be delivered by your Windows Server; meaning that your authentication runs locally, rather than in the cloud environment. You may already have a hybrid environment, meaning that your services run both locally and within the cloud – and if you do, the best practice advice provided by the NCSC¹⁰ is that businesses should defer to the cloud-based authentication, rather than rely on their older locally based services to support this function, as it is more secure and cohesive with other SSO (Single Sign On) cloud-based services to run this function within the one ecosystem.
Need to achieve peace of mind?
If you are carrying any uncertainty or are not sure where to turn on starting to implement best security practices to defend your small business within Microsoft 365, we can help. At Edge IT, we have years of experience in delivering tailored, compliant and technically-secure cloud environments to operationally benefit small businesses across London and the Home Counties, from our base in Hertfordshire.
Whether you are looking to implement Microsoft 365 for the first time, or need to get more from your existing environment, please reach out to our team today to explore your needs and our solutions.
¹ https://www.hiscoxgroup.com/news/press-releases/2018/18-10-18
⁵ https://docs.microsoft.com/en-us/sharepoint/turn-external-sharing-on-or-off
⁶ https://docs.microsoft.com/en-us/sharepoint/change-external-sharing-site
⁷ https://docs.microsoft.com/en-us/microsoftteams/teams-dependencies
¹⁰ https://www.ncsc.gov.uk/blog-post/securing-office-365-with-better-configuration
Edge IT Can Help
Edge IT Can Help
Technology should empower your business, not hold it back. We provide proactive IT support, robust cybersecurity, and seamless solutions to keep your organisation secure and running smoothly. Get in touch today and let’s strengthen your IT for a smarter, safer future.
Edge IT Can Help
Technology should empower your business, not hold it back. We provide proactive IT support, robust cybersecurity, and seamless solutions to keep your organisation secure and running smoothly.
Get in touch today and let’s strengthen your IT for a smarter, safer future.